Identity Federation with SAML and Active Directory
Following our exploration of IAM Users, Groups, and Roles, let’s look at Identity Federation with SAML and Active Directory. For the AWS Certified Solutions Architect Associate exam, there are probably at best just a few questions. However, if you're like me, having some background on this concept and being able to answer the question if it appears is a bonus.
Authentication using Active Directory at AWS is a concept that may appear on the exam, particularly in questions related to accessing shared storage hosted by FSX for Windows File Server.
Identity Federation
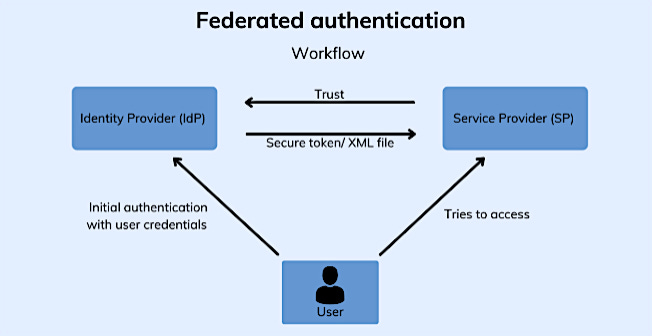
Identity is one of the key roles of identity and access management (IAM) performed at AWS; if a request cannot be identified, it is denied.
Adding the term “Federation” to the discussion, let’s first review the definition: “A federation is an organizational system where multiple entities unite under a central authority while retaining a degree of autonomy.”
The “central authority” in this case is AWS. The “entities” are external identity providers such as Google, Facebook, Microsoft, or Apple that verify a person's identity.
Figure 1: Federated Authentication
Back in The Day ….
Back in 2000, before the public cloud and the Internet had evolved into their current forms, many corporations were running Microsoft’s Active Directory. Active Directory was a corporate network necessity as most mid-to-large-sized corporations ran Microsoft Exchange, which utilized Active Directory for user authentication.
Active Directory was the Kerberos authentication domain used to verify your identity, and once successful, access to your email and other services was granted.
It’s hard to remember a world where the Internet was not an integral part of everyone’s life. From 2000 to 2005, corporations were grappling with their own in-house DNS deployments, local email, and queue-based printing.
Today, you could still maintain a deployment of Active Directory Federation Service and Exchange; however, the Microsoft 365 cloud is probably where the deployment is hosted as a subscription service.
The current version of Microsoft Exchange Server is Exchange Server 2019, released in 2019, meaning that the tag team of Active Directory and Exchange still has a stable shelf life running in the public cloud as a SaaS service.
Today, identity federation enables access to AWS resources using external identity providers (IdPs), including Active Directory with the SAML protocol, as well as other external providers such as Facebook, Google, Microsoft, and Apple, which utilize OpenID and OAuth protocols.
Identity federation allows corporate users to access AWS resources using IAM Roles using credentials from an external IdP, such as Active Directory, to identify the requests for access.
Let’s break down the key components and configurations for SAML-based federation with Active Directory so you can successfully navigate any exam test questions on this topic.
Understanding Identity Federation using SAML
The Security Assertion Markup Language (SAML) 2.0 is a widely adopted standard for exchanging authentication and authorization data between Active Directory and the service provider (SP), in this case, AWS. SAML enables single sign-on (SSO) across these two separate systems. This is ideal for enterprises where employees have already logged onto the corporate network once and wish to use the same corporate credentials to access AWS cloud resources.
Identity federation utilizing SAML 2.0 enables users to sign in to AWS using credentials from an external IdP, typically Active Directory, and receive temporary AWS credentials to access resources.
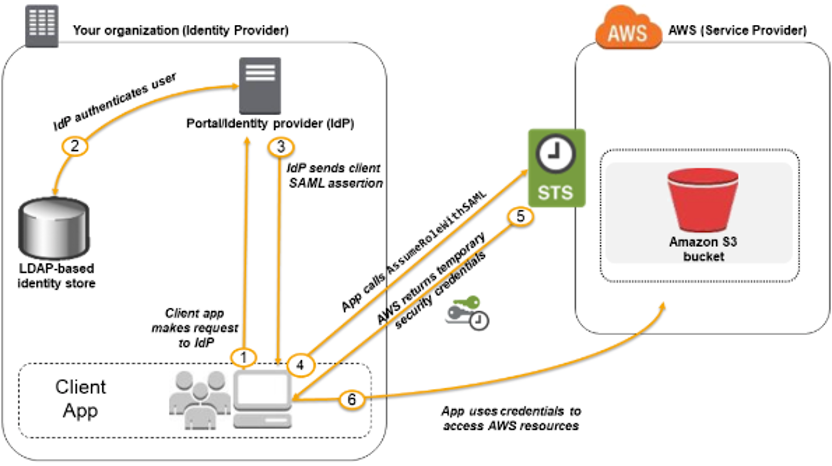
User Authentication: A user first authenticates with the IdP (AD FS) using their corporate credentials.
SAML Assertion: The IdP generates a SAML assertion, a digitally signed XML document containing the authenticated user’s identity and applicable permissions.
AWS STS Interaction: The user exchanges the SAML assertion with the AWS Security Token Service (STS) via the AssumeRoleWithSAML API. Once the user’s identity is confirmed, STS grants temporary AWS credentials allowing the user access to permitted AWS resources, such as the AWS Management Console or programmatic access via CLI/SDKs.
Figure 2: Identity Federation overview
Identity Federation reduces the need for IAM user accounts, centralizes identity management, and provides temporary credentials, aligning with established security best practices.
Enter the AD Connector
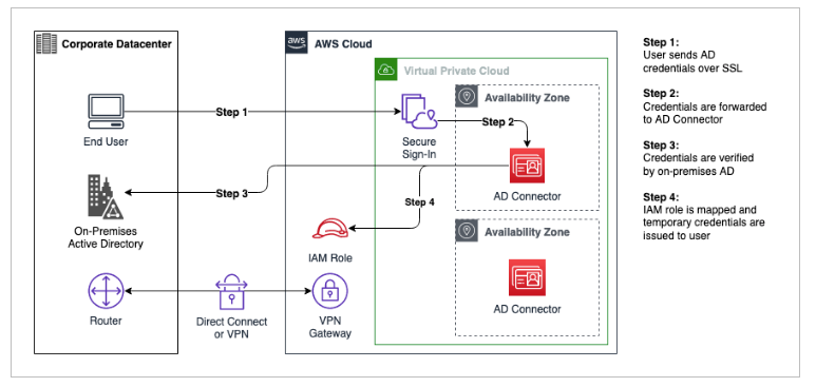
A question you may be thinking: How does AWS get up-to-date information about the authenticating user? The answer to this question is facilitated by a component called the Active Directory connector.
AD Connector establishes a trusted relationship between your Active Directory and AWS. When AD Connector is configured, the trust allows you to carry out the following tasks:
Sign in to AWS applications by using your Active Directory credentials, such as Amazon WorkSpaces, Amazon WorkDocs, and Amazon WorkMail.
Provide federated sign-in to the AWS Management Console by mapping Active Directory identities to AWS Identity and Access Management (IAM) roles.
The AD Connector serves as a directory gateway, enabling seamless integration between your on-premises Microsoft Active Directory (AD) and AWS services. The connector forwards authentication and directory queries from AWS applications or AWS SSO to your on-premises Active Directory. Users authenticate using their existing AD credentials, enabling single sign-on (SSO) without needing to replicate directory data to the cloud.
Figure 3: Authentication flow
Before the AD connector can be operational, a trust relationship must be created between AWS and Active Directory.
· Active Directory Federation Services (ADFS) must be configured for Active Directory to trust AWS as a relying party. AWS metadata must be downloaded to the Active Directory Federation Services deployment that will communicate with AWS Security Token Services.
· Next, a SAML identity provider must be configured by creating an IAM Identity Provider and uploading Active Directory’s metadata document from AD FS. This completes the trust relationship between AWS STS and AD FS.
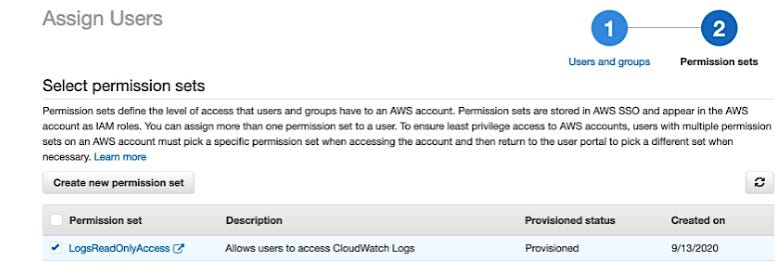
· Finally, permission sets must be created and assigned that define what federated users can do after they have been vetted and approved, for example, LogsReadOnlyAccess.
Figure 4: Permission sets define assigned IAM Roles
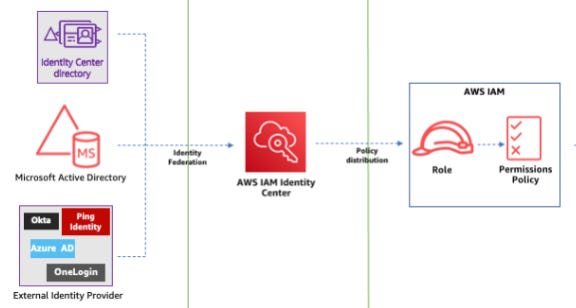
AWS Identity Center
AWS Single Sign-On has been replaced by the AWS Identity and Access Management (IAM) Center.
AWS IAM Identity Center is a managed SSO service that centralizes access to AWS accounts, AWS-managed applications (such as Amazon Q and SageMaker Studio), and SAML 2.0-enabled third-party applications (including Microsoft 365 and Salesforce). It also supports multiple third-party external identity sources, such as Okta, Microsoft Entra ID, and its own Identity Center directory.
Figure 5: IAM Identity Center integration
The Managed Microsoft AD service can also be deployed on AWS as a fully managed Active Directory deployment, supporting multi-domain and forest setups.
Integrating AWS Managed Microsoft Active Directory with AWS IAM Identity Center enables centralized user management and single sign-on for AWS accounts and applications using existing Active Directory credentials.
Best Practices for Identity Federation
Use Temporary Credentials: Federation provides temporary credentials that are assigned and managed by the Secure Token Service (STS), thereby reducing the risk of long-term credential exposure.
Centralized identity management: By leveraging existing AD infrastructure to avoid duplicating user accounts in IAM.
Monitor access: using AWS CloudTrail to log AssumeRoleWithSAML calls, ensuring visibility into federated access.
Exam Tips for Identity Federation
· For the SAA-C03 exam, focus on these key concepts related to identity federation:
· SAML 2.0 is used for web-based SSO.
· OpenID Connect (OIDC) is used for mobile apps.
· SAML is more common for enterprise Active Directory integration.
· Managed AD to IAM Identity Center integration allows users to access AWS resources with their corporate AD identities.
· Choose AD Connector for simple hybrid Single Sign On with an existing Active Directory deployment.
· Use Managed Microsoft AD for multi-domain or cloud-native Active Directory needs.
· Federated users assume IAM roles via AssumeRoleWithSAML, requiring a trust policy specifying the IdP.
· Federation provides temporary credentials, aligning with best security practices. Understand their lifecycle (e.g., default 1-hour duration, configurable up to 12 hours).
· For exam questions, identify whether federation is needed (e.g., enterprise users accessing AWS) and select SAML for AD integration over creating IAM users.
· When a question involves enterprise users accessing AWS with corporate credentials, choose SAML-based federation or AWS SSO over creating individual IAM users, as this aligns with best practices for scalability and security.
· IAM SAML Federation is ideal for organizations with established SAML-based identity systems wanting direct integration with AWS IAM roles.
· IAM Identity Center suits businesses using AWS Organizations or seeking a managed, user-friendly SSO solution with broader support for mobile applications.
Sample Exam Questions
Here are three sample questions to test your understanding of identity federation with SAML and Active Directory, each with two correct answers, two incorrect answers, and explanations referencing AWS documentation.
Question 1
Which steps are required to configure SAML 2.0 federation with Active Directory for AWS access? (Choose two.)
A. Create an IAM role with a trust policy for the SAML provider.
B. Create IAM users for each Active Directory user.
C. Upload the IdP’s metadata document to AWS IAM.
D. Assign IAM groups to Active Directory users.
Correct Answers: A, C
Explanation:
A is correct because an IAM role with a trust policy specifying the SAML provider (e.g., AD FS) is required for federation.
C is correct because uploading the IdP’s metadata document to AWS IAM establishes the trust relationship.
B is incorrect because federation avoids creating IAM users for each AD user.
D is incorrect because IAM groups are not directly assigned to AD users; instead, AD groups map to IAM roles via SAML attributes.
Question 2
What are the benefits of using SAML-based federation with AWS? (Choose two.)
A. Provides temporary AWS credentials for users.
B. Eliminates the need for IAM roles.
C. Centralizes identity management with an external IdP.
D. Allows permanent access keys for programmatic access.
Correct Answers: A, C
Explanation:
A is correct because SAML federation provides temporary credentials via AWS STS, enhancing security.
C is correct because federation centralizes identity management with an external IdP like AD FS.
B is incorrect because SAML federation relies on IAM roles, not eliminates them.
D is incorrect because federation uses temporary credentials, not permanent access keys, which are associated with IAM users.
Question 3
A company wants employees to use their Active Directory credentials to access the AWS Management Console. Which AWS service or feature should they use? (Choose two.)
A. AWS Identity Center with AD Connector.
B. IAM SAML 2.0 identity provider with AD FS.
C. IAM user accounts with long-term credentials.
D. Amazon Cognito user pools.
Correct Answers: A, B
Explanation:
A is correct because AWS SSO with AD Connector enables SSO for AD users to access the AWS Management Console.
B is correct because an IAM SAML 2.0 identity provider with AD FS allows AD users to access AWS via federation.
C is incorrect because creating IAM user accounts with long-term credentials is not recommended for AD integration.
D is incorrect because Amazon Cognito user pools are used for application authentication, not enterprise AD integration for console access.