Welcome to the third blog post in my 100-blog series to help you pass the AWS Certified Solutions Architect - Associate (SAA-C03) exam.
Following our exploration of IAM Users, Groups, and Roles, as well as identity federation with SAML, let’s examine the purpose and functionality of IAM access keys and Multi-Factor Authentication (MFA), both critical components of AWS IAM security.
Access Keys and MFA are part of the "Design Secure Architectures" domain, which accounts for 30% of the SAA-C03 exam.
This post will explain how access keys function in authenticating IAM users for the management console, AWS CLI access, and SDK API calls. I will also discuss multi-factor authentication (MFA), best practices, exam-focused tips, and end with some sample questions to help you prepare for the SAA-C03 exam.
Access Keys
Access keys are essential components of AWS Identity and Access Management (IAM). They are used for authenticating IAM users and granting programmatic access to AWS services. Access keys form part of long-term security measures. When an IAM user is created and assigned access keys, the user account remains active until the access key is disabled or the IAM user is deleted.
Fun fact for 2025: Creating an IAM user does not automatically generate access keys (both the access key and secret access key). Only after the IAM user has been created can long-term access keys be generated and linked to the selected IAM user. Check out the video below.
The “access key” consists of two linked parts: an access key ID and a secret access key. The access key ID uniquely identifies the IAM user. The secret access key is a cryptographic secret used to sign API requests.
For browser-based access to the AWS Management Console, access keys are verified in the background to ensure they match the IAM username and password.
The access key ID identifies the IAM user, and the secret access key creates a cryptographic signature. AWS verifies the signature to authenticate the user and checks IAM policies to approve any requested tasks. The cryptographic signature is validated against every API request.
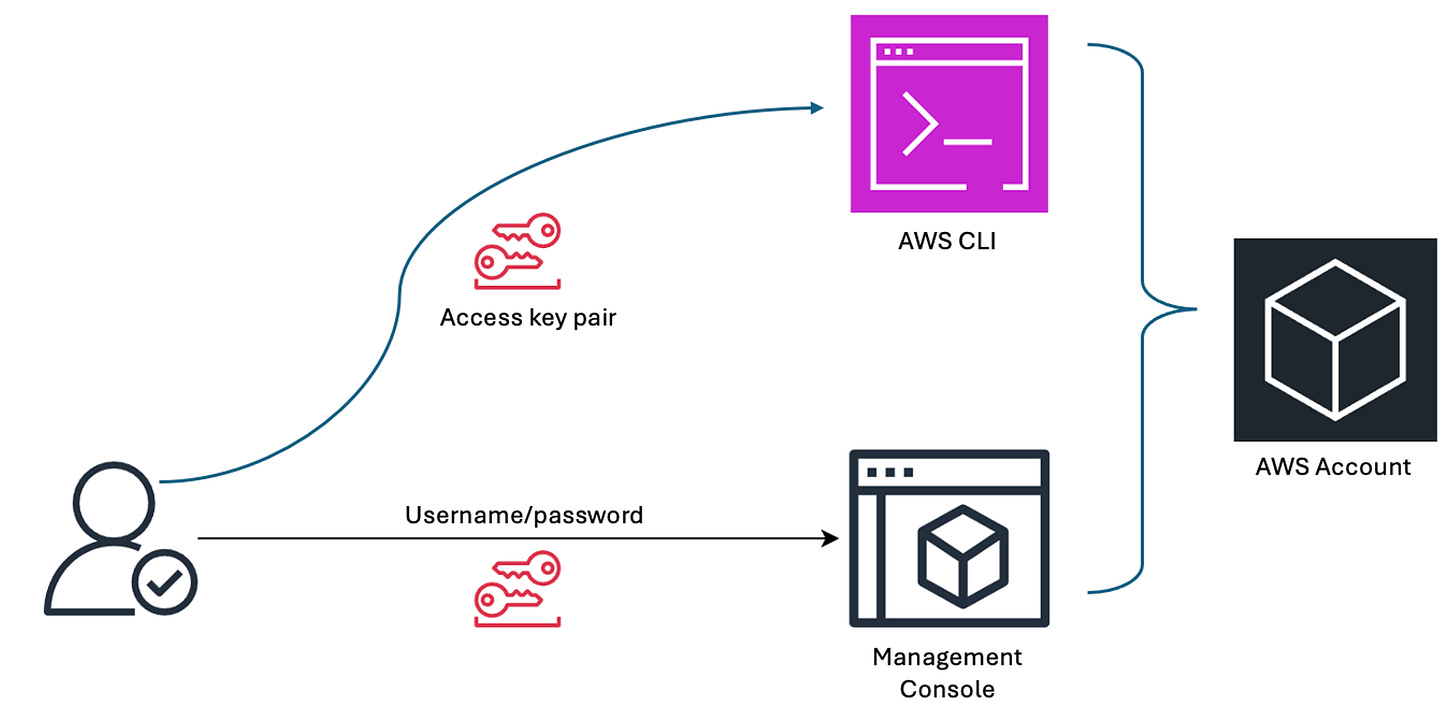
An IAM user can be set up with both a username and password for console access, as well as access keys for programmatic access. This allows the same user to perform tasks using the management console or the AWS CLI interface. MFA can also be required for console access, increasing security.
Figure 1: Access keys are used for both AWS CLI and console access.
Programmatic Access Using a Software Development Kit
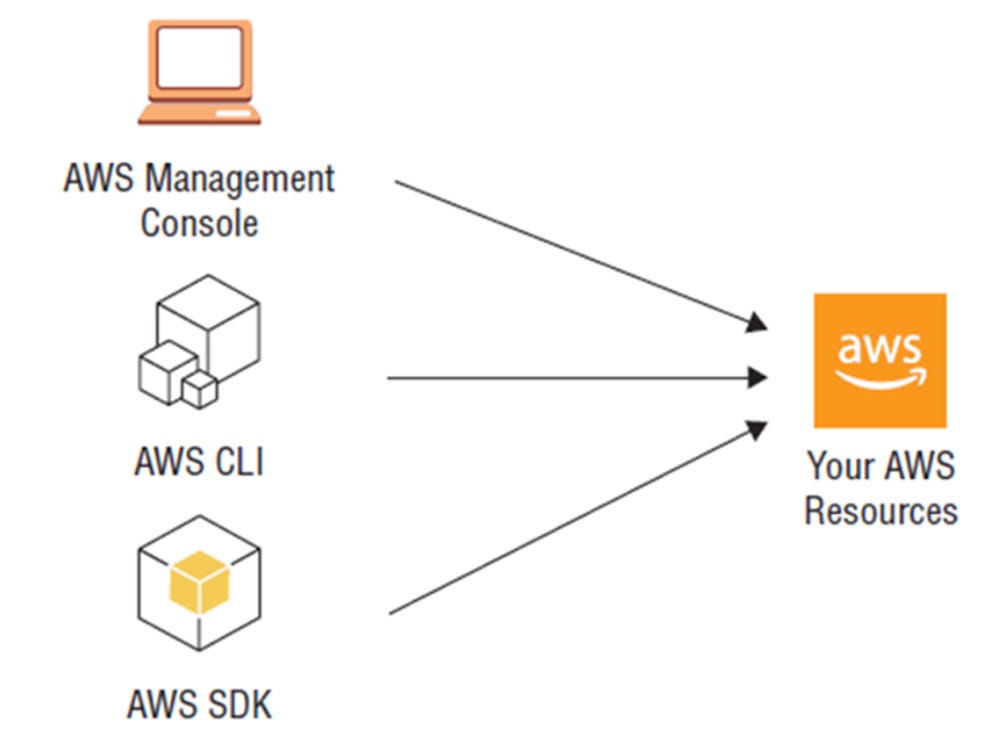
Software development kits (SDKs) enable developers to integrate AWS services into applications, such as storing files in S3 storage, querying a DynamoDB table, or invoking Lambda functions.
Figure 2: SDKs are used to integrate AWS services into applications.
The SDK API requests use temporary credentials obtained from AWS Security Token Service (STS), which include an Access Key ID, a Secret Access Key, and a Session Token. These security credentials differ from long-term access keys because they are temporary, with a limited lifespan (e.g., 15 minutes to 36 hours, depending on configuration), and they automatically expire. This reduces the risk of misuse compared to permanent access keys.
SDKs automatically sign API requests using the AWS Signature Version 4 (SigV4) protocol, incorporating the secret access key, request details, timestamp, AWS region, and the cryptographic signature.
Multi-Factor Authentication
MFA requires users to provide two or more authentication factors: something they know (such as a password) and something they have (a code generated from an authenticator app or a hardware device).
Figure 3: MFA typically uses a software app like Authy or Google Authenticator.
In AWS, MFA can secure any IAM user and the AWS account root user, protecting against credential compromise. Supported devices include:
Virtual MFA: Apps like Google Authenticator, Microsoft Authenticator, or Authy generate time-based one-time passwords (TOTPs).
Hardware MFA: Physical devices like Gemalto tokens or YubiKeys.
Configuration Steps for IAM Users
From the AWS Management Console, search and select IAM, choose an IAM User, and then click on Security Credentials.
Use Case: An administrator requires MFA for secure access to the AWS Management Console to manage S3 buckets, ensuring that even if their password is compromised, unauthorized access is blocked. Use IAM policies to enforce MFA for deleting S3 objects.
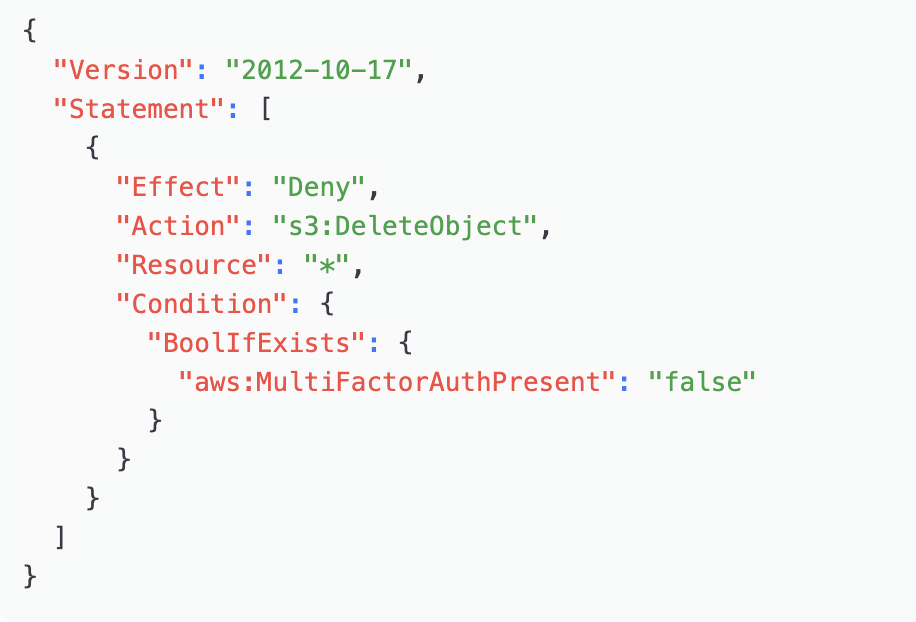
Figure 4: AWS:MultiFactorAuthPresent: “false” ensures MFA must be used for gaining access.
Exam Tips For the SAA-C03 Exam
Access Key Management: Rotate access keys every 90 days to help reduce the risk of compromised credentials. AWS allows two active access keys per IAM user to ensure a smooth transition during key rotation.
Monitoring: Utilize AWS CloudTrail to log API calls and console sign-ins using access keys, enabling the identification of who accessed what and when.
Roles: Programmatic and console access with IAM roles that utilize temporary credentials is preferred over access keys to minimize long-term credential risks.
MFA Enforcement: Apply IAM policies with conditions, like aws:MultiFactorAuthPresent, to require MFA for sensitive actions, including S3 deletions and console access.
Root User Security: Always activate MFA for the root user, since it has unrestricted access to all AWS account resources.
Scenario Analysis: For questions involving secure console or programmatic access, prioritize MFA with username/password for console access, access keys for CLI/SDK, and IAM roles for services, ensuring least privilege.
Pro Tip: If a question involves an IAM user accessing the AWS Management Console or S3 programmatically, enable MFA for console access and use access keys for API calls. Store keys securely and enforce least privilege through IAM policies.
Sample Exam Questions
Question 1: Which configuration secures an IAM user’s access to the AWS Management Console and S3 programmatically? (Choose two.)
A. Enable Multi-Factor Authentication (MFA) for the IAM user’s console access.
B. Store access keys in a public repository for console and API access.
C. Attach an IAM policy requiring MFA for sensitive actions like deleting S3 objects.
D. Use the root user credentials for console sign-in.
Correct Answers: A, C
Explanation:
A is correct because enabling MFA secures console access.
B is incorrect because publicly storing access keys is insecure.
C is correct because IAM policies can enforce MFA for sensitive actions by using conditions like aws:MultiFactorAuthPresent.
D is incorrect because the root user is not an IAM user and should not be used for console sign-in.
Question 2: How should a system administrator secure an IAM user authenticating to the AWS Management Console and CLI for S3 access? (Choose two.)
A. Create an access key for the IAM user and set it up in the AWS CLI.
B. Embed the secret access key directly into a script for console access.
C. Enable MFA for the IAM user’s console sign-in.
D. Make the S3 bucket publicly accessible.
Correct Answers: A, C
Explanation:
A is correct because access keys set up in the AWS CLI facilitate secure IAM user authentication for API calls.
B is incorrect because hardcoding secret access keys is insecure for both API and console access.
C is correct because enabling MFA protects console sign-in, including when using access keys.
D is incorrect because public S3 access breaches security principles.
Question 3: Which configurations improve security for an IAM user authenticating API calls and AWS Management Console access?
A. Store access keys in AWS Secrets Manager for API and console authentication.
B. Restrict access to devices with MFA enabled.
C. Attach an IAM policy that grants only the permissions necessary for API and console actions.
D. Share access keys with team members for console access.
Correct Answers: B, C
Explanation:
A is incorrect because storing IAM access keys in AWS Secrets Manager for authentication to AWS isn't its intended purpose. AWS Secrets Manager simplifies managing and securing sensitive third-party information like database credentials, API keys, and other corporate secrets.
B is correct because defining access with MFA is a security best practice.
C is correct because least privilege policies limit actions for both API and console access.
D is incorrect because sharing access keys is insecure.